 What is Ransomware?
What is Ransomware?
ZDNet reported in September, 2016 the cost of ransomware could reach $1Billion in 2016. To show the scope of this epidemic, in 2015 the total paid out to criminals was estimated to be $24Million. No small amount, but the jump in one year is STAGGERING to say the least. Don’t even know what ransomware is? Do you even need to be worried about it? Maybe it only affects huge businesses and I don’t even need to worry. Sadly, the reality & the statistics say otherwise. We’ll explain ransomware & ways to thwart it from being a disaster for your business.
Ransomware, a practical Hollywood style Example
Remember the movie “Risky Business” with a very young Tom Cruise as the character Joel? The plot surrounds Joel being forced to pay criminals who came and took every single possession in the parents’ house and ransomed the possessions back to Joel. Here’s a 2 minute clip from the movie to refresh your memory.
That’s what ransomware does. The criminal takes all of your business’ digital possessions and holds them hostage for money. That’s the 10 second explanation. If that creates a clear picture in your mind what a ransomware attack looks like, great. If the only thing you remember about the movie is Tom Cruise singing in his underwear, please continue to read this article. By the end, you will have a very clear picture of what happens with this cybercrime.
Where’s the Fire? (Why an Epidemic Now?)
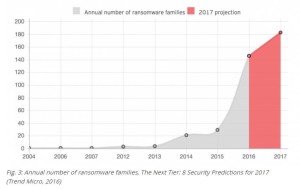
Ransomware wasn’t a widespread threat until around 2013. The first versions of the malware only impacted individual PCs. Annoying, but not worthy of huge sums of money. As new versions got nastier, the threat increased. By 2014, network data was targeted. By 2016, not only your network data, but your backed up data as well, particularly if you used something like “Back up Exec.” It even happened to Madison County in Indiana. See the story here. The bit of good news in all this was no data left your business, so no data breach regulations were triggered. No need to alert your clients your computer security was compromised. No bad PR, just internal embarrassment. That’s changing in 2017 with versions of ransomware now sending the criminals your data before they even let you know about any ransom. Should the breach happen, you WILL be required to alert your customers about your attack. The general public finding out won’t be far behind. Your competition is just waiting for this to happen. Most importantly, the biggest reason this has become an epidemic is due to the economic model behind it. This is a huge money maker (high reward) with very low risk of punishment. There’s no incentive for the criminals to stop & worse still, incentive for more criminals to join in the profit taking. Our best chance of derailing this is to not pay the ransom. The only way to accomplish this is to plan our defenses carefully.
How an Attack Originates
It can come through in a Phishing SPAM email, clicking on a website, even a previously good website might have been hacked, or on an infected Flash Drive someone brought in from home. Your employees may do everything correctly, and still get attacked. I liken it to being held at gunpoint & robbed in the middle of the day.
Why Your Anti-virus (AV) Isn’t Enough
 Most AV products, such as Kaspersky, Trend Micro, BitDefender, are behind the curve ball on ransomware. They depend on recognizing “the make & model” or make = “family” of the ransomware. If ransomware were a car, this would be no big deal. A few new models each year would be easy to track. But the criminals create thousands of new models every DAY. Until your particular AV has seen and declared one of those models “bad” you’re at huge risk because the AV won’t stop it. These are known as zero-day threats. Rather than looking for the make & model, we need to look at the driving behavior. Is it dangerous? Should we stop that “car” for the way it’s being driven?
Most AV products, such as Kaspersky, Trend Micro, BitDefender, are behind the curve ball on ransomware. They depend on recognizing “the make & model” or make = “family” of the ransomware. If ransomware were a car, this would be no big deal. A few new models each year would be easy to track. But the criminals create thousands of new models every DAY. Until your particular AV has seen and declared one of those models “bad” you’re at huge risk because the AV won’t stop it. These are known as zero-day threats. Rather than looking for the make & model, we need to look at the driving behavior. Is it dangerous? Should we stop that “car” for the way it’s being driven?
Behavior Driven Protection
Sophos just released their first AV replacement based on this concept, Intercept X. As a Sophos partner, we’re excited to represent this leap forward. We also work with SentinelOne which has been utilizing this concept much longer. We currently recommend it for the “after an attempted attack” forensics which is included with the product. Before SentinelOne, once you were attacked you only had 2 choices, pay the ransom or restore your last good backup. (Which is why modern backups are so critical.) But now with SentinelOne, there’s another choice; Rollback the changes
Employees Trained to Recognize Ransomware Attacks
Through simple lunch & learn training sessions your employees can learn to avoid 90% of the attacks coming through emails. Think of it as Defensive Driving for your employees. Even if this costs the company a small amount of money, think of it as necessary skills training for your employees. You can also promote it as an employee benefit as it will assist them with their personal email as well.
Ransomware Are the Landmines You Don’t Want Your Business to Step On
As you can see this is an avoidable disaster. Training and the proper tools can prevent this from ever being a problem you’ll have to confront. One last cautionary tale. I had an 11 person professional services firm contact me a month after I’d proposed stronger cybersecurity solutions. They hadn’t taken any action on my proposal, but called to say they had been attacked by Crypto-Wall, a model of ransomware. Their Kaspersky AV allowed the attack as it didn’t recognize the “model” as being malware. Something else the owner wasn’t aware of at the time, their backups hadn’t been working for 5 days. They didn’t pay the ransom, but lost 7 days of productivity as well as untold hours attempting to verify the restored information over the next several months. Don’t wait for the disaster, take action now.

 Contact Us At
Contact Us At

